What Is Remote Access? Definition and Best Software List
Remote work is on the rise in today’s digital era. Even in cases where employees live and work within the same city, many opt for regular work from home hours. According to Gallup’s State of the American Workplace survey, 43% of employees worked remotely in some capacity in 2016, a 39% increase from 2012. On a global scale, IWG found 70% of employees work remotely at least one day a week.
But what is remote access, and how do employees and tech gurus use it to become more efficient and effective? The simple remote access definition is this: any application empowering users to remotely access another computer, no matter how far away it is.
Both paid and free remote access software are available today. The platform you decide to use depends on the size of your organization and your unique business goals. My personal favorite is SolarWinds® Dameware® Remote Everywhere (DRE). This robust remote access software offers a host of user-friendly features designed to grow with your business and facilitate troubleshooting.
Feel free to jump ahead to a specific topic:
- Use Cases for Remote Access Software
What Is Remote Desktop Access?
What Is Unattended Remote Access?
What Is Remote Access Used For? - How to Gain Remote Access
- Remote Access Security Best Practices
- What to Look For in Remote Access Software
- Best Remote Access Software
✓ SolarWinds Dameware Remote Everywhere
✓ SolarWinds Dameware Remote Support
✓ RemotePC
✓ TeamViewer
✓ Zoho Assist
✓ Splashtop - Best Free Remote Desktop Software
✓ Chrome Remote Desktop
✓ Microsoft Remote Desktop
✓ Remote Utilities - Remote Access Simplified
Use Cases for Remote Access Software
The most common remote access definition is any type of software granting access to a remote computer. But this definition only scratches the surface of everything remote access encompasses. The purpose and function of remote access varies greatly, and it depends on the user and the specific platform in use. Remote access tools can be on demand or unattended, and they may connect users to remote resources or provide access to the host computer from other locations.
What is remote access for
improve productivity
Drive collaboration

Provide technical support
What Is Remote Desktop Access
Remote access enables users to connect to resources in other locations. Remote desktop access tools take this further, allowing users to control the host computer from any location via the internet.
What Is Unattended Remote Access?
With unattended remote access, as opposed to spontaneous or on-demand remote access, remote agents are installed on all remote devices or servers. This allows users to access these devices at any time without needing to wait for the host device to accept the connection.
What Is Remote Access Used For?
Here are a few of the most common applications for remote access:
- Improve Productivity From Afar: Individual users can leverage remote desktop access to view and edit their files as easily as if they were sitting in their normal cubicle or corner office. This helps keep productivity up when an employee is traveling or when they need to work from home. Programs like Microsoft OneDrive, Dropbox, and Google Drive are a few of the most common platforms empowering employees to access and edit their documents outside of the local area network.
- Drive Collaboration Among Dispersed Teams: A company may be headquartered in New York but have satellite offices in Zurich, Raleigh, or Chicago. Keeping teams aligned when they’re separated by miles, mountains, and oceans is no easy task. This is where remote access comes into play. Remote access helps facilitate peer-to-peer relationships via screen sharing for training demonstrations and large team meetings. Many employees feel as if they’re in the same room as their cross-continental colleagues.
- Provide Technical Support: This is perhaps the most common application of remote access among IT technicians. Leveraging robust remote access software, IT administrators and their teams are empowered to directly control the workstations—including the desktop, mouse, keyboard, and everything else—of their employees, no matter where they are. When an issue arises, whether it’s an application failing to open or a document refusing to download, IT teams can easily connect to user workstations to troubleshoot the problem.
How to Gain Remote Access
Remote access has evolved tremendously over the last decade. To gain remote access in today’s technology-driven landscape, remote access software must be deployed over the network on a remote access server or installed on a local workstation known as the “client.” The workstation you remotely access is the “server” in the popular client–server relationship. Here are a few of the most common ways to achieve this remote connection:
- Virtual Private Network (VPN): VPNs allow employees working remotely to route their online activity through a secure server capable of connecting them directly to their company’s network. These systems encrypt data sent over the network to ensure it’s unreadable, even to those who can gain access to it.
- Virtual Network Computing (VNC): VNC is a form of graphical screen sharing used to view and control the desktop of another computer. This is accomplished using the Remote Framebuffer protocol over a network connection. A viewer is installed on the client and connected to the server (the remote workstation). VNC is typically conducted over a VPN.
- Remote Desktop Protocol (RDP): RDP is a proprietary Microsoft protocol used to achieve a remote connection, but there are also versions for MacOS, Linux, and other operating systems. In some cases, software companies may even have their own proprietary protocols. RDP allows the server to listen on TCP port 3389 and UDP port 3389 and approves a connection once a request is made.
- Internet Proxy Servers: Internet proxy servers are used to facilitate a connection outside of a corporate network or firewall. Though this option is instrumental when it comes to creating outside connections, a remote access connection is usually made over a secure VPN.
Remote Access Security Best Practices
Since we’ve defined it, it’s time to discuss the best practices associated with remote access software. While each of the best practices listed below is unique, they all have one thing in common: a focus on security.
Modern-day remote access is highly convenient and effective, but it’s not risk-free. Cybercrimes are on the rise. Today’s IT administrators must be more diligent than ever before to keep cunning hackers at bay and protect exposed remote connections. Whether you’re educating your employees on remote access for work or coaching your technicians on remote access for tech support, here are a few security best practices to keep top of mind:
- Put Endpoint Protection Into Play: Endpoint security involves securing the servers, workstations, and devices you use to connect to networks. Patch updates, antivirus software, and firewalls are a few examples of endpoint security in action.
- Find a Secure Connection: While free and highly convenient, public Wi-Fi carries a whole slew of cybersecurity risks. Invisible attackers will often sit on a public Wi-Fi network and eavesdrop on passing traffic, waiting to snatch passwords or other sensitive data. Warn employees of the risks involved with securing sensitive work documents over public Wi-Fi.
- Avoid Using Personal Devices for Work: Personal laptops, tablets, and mobile devices are often not equipped with the same patch updates and antivirus software as company-owned devices. Employees who use their personal devices to work remotely can put company networks in jeopardy, as they’re more likely to expose their systems to malware and other cybersecurity threats. If employees must use their own devices, it’s up to IT technicians to develop a BYOD (or bring-your-own-device) policy outlining strict security measures.
- Develop Complex Passwords: Passwords for network logins should always be at least eight characters (preferably closer to 15), contain a healthy mix of characters (numbers, symbols, varying cases, etc.), and never contain parts of the username/login or personal information. IT technicians must not only adhere to these best practices but enforce them among all members of their staff.
- Implement Multi-Factor Authentication: One-factor authentication is no longer a reliable way to protect against security breaches. Multi-factor authentication is now a must. It doesn’t matter which authentication practices you implement; as long as you have a two-step process in place, you drastically improve your protection against hackers. Sophisticated remote access software will often rely on smart card login, in which a user must have possession of a physical smart card as well as a private PIN. This simple step goes a long way toward protecting your entire network.
- Leverage Password Protection Systems: Once you’ve designed complex, secure network passwords, you must store them in a safe space. Vault-protected password management solutions are one example of a storage tool many IT professionals turn to for compliance-grade security.
What to Look For in Remote Access Software
Cloud-based programs like Dropbox and Google Drive have empowered employees to gain access to files and folders from any location and at any time of day. But these programs don’t provide IT technicians with the level of control they need to remotely troubleshoot end-user issues and quickly resolve the IT tickets flooding their help desk. Fortunately, sophisticated remote access software has evolved to take care of this.
With so much available remote access software, it can be hard to find the right one for your unique business needs and goals. I recommend looking for a product capable of checking the following boxes:
- Secure Connections: A secure remote connection is critical when it comes to keeping your IT infrastructure out of harm’s way. Robust remote access software will leverage two-factor authentication (like smart card login) and encryption methods like RSA and RC4 to keep your data safe and secure.
- Comprehensive Troubleshooting: Being able to dig in and remotely resolve end-user issues requires software capable of running local batch scripts in a system shell setting, taking screenshots and recordings during active sessions, and restarting and shutting down a PC with ease.
- Consistent Communication: Troubleshooting an IT issue often involves consistent communication with the end user to find out exactly what went wrong, when it happened, and how the problem arose in the first place. Look for tools offering live chat, videoconferencing, and technician screen sharing to facilitate communication with end users.
- Help Desk Integration: Regardless of the size of your organization, help desk tickets are an inevitable reality. Remote access software helps streamline the ticketing process by establishing a parent-child relationship with your help desk. This makes it easier to initiate remote assistance directly from a ticket, save remote session metadata, and keep end users up-to-date on the status of their tickets.
- Active Directory Integration: In certain cases, remote access tools can even integrate with Active Directory. This is a capability I’ve come to consider crucial, as it helps centralize and manage IT sign-ins. Active Directory integration makes it easier to reset passwords for end users; add, delete, and update Active Directory users, groups, and OUs; and manage multiple Active Directory domains from a unified console.
- Scalability: On-premises remote control software allows IT administrators to perform mass deployments and integrate with an unlimited number of end users. The right tool will grow with your business, helping your team provide comprehensive support to tens, hundreds, or thousands of employees.
Best Remote Access Software
I’ve talked about the attributes to look for in remote access software, but how can you be sure you’re investing your company’s resources in the right product? To answer the question of what the best remote access software is, here are my favorite paid tools:
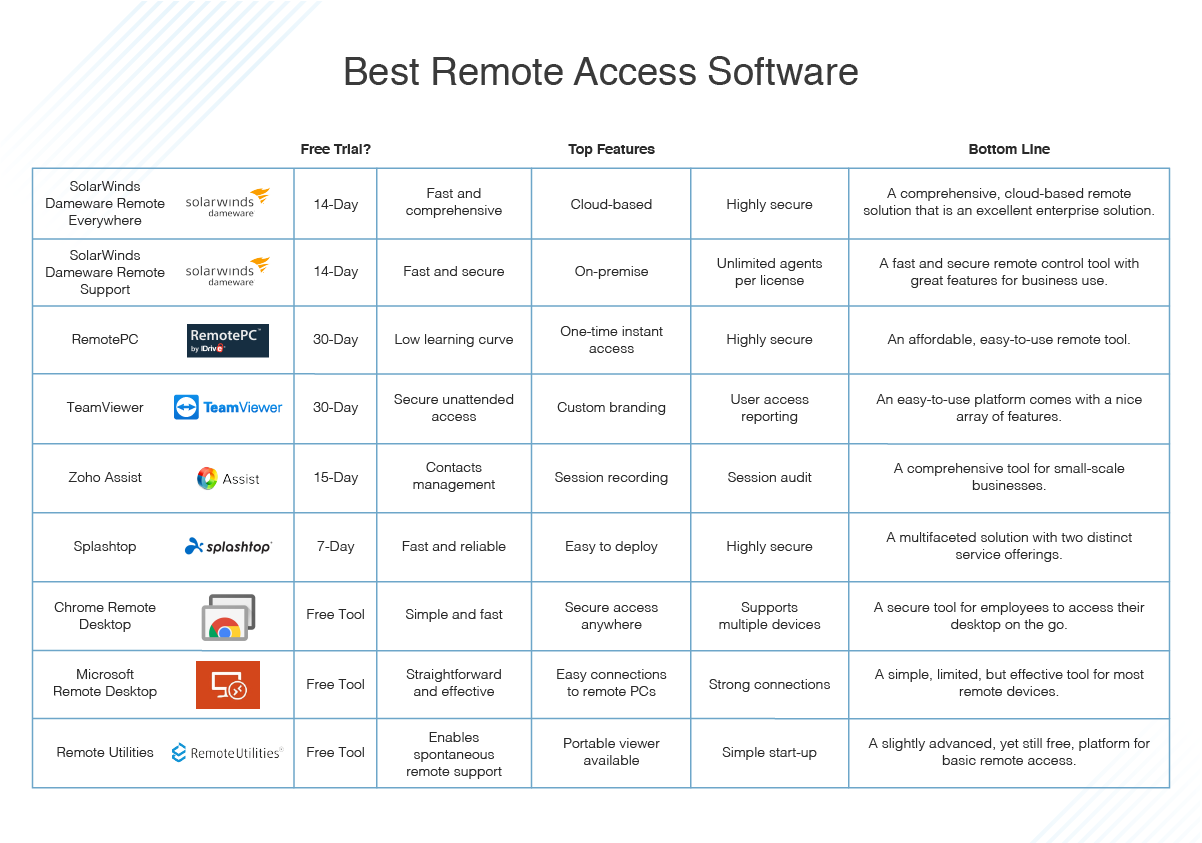
SolarWinds Dameware Remote Everywhere
Dameware Remote Everywhere (DRE) from SolarWinds is hands-down my favorite remote support software. This incredibly powerful, cloud-based remote solution empowers IT professionals to access nearly any platform or device. Powered off, sleeping, and even crashed workstations can be accessed via Intel vPro with AMT, Wake-on-LAN, and KVM. This means technicians don’t have to wait for a user to get back to their computer before they can begin troubleshooting.
DRE further facilitates the resolution process through screen sharing, live chat, and videoconferencing. These features help keep end users up to speed and in the loop while simultaneously allowing technicians to gather the critical details and data they need to resolve issues quickly and efficiently.
But security is even more important than speed and efficiency, and in this area, DRE is second to none. The platform implements advanced encryption protocols, two-factor authentication, and multilevel permissions designed to protect your company from even the most advanced hackers.
SolarWinds Dameware Remote Support
Another remote access offering from SolarWinds, Dameware Remote Support (DRS) is an on-premises software with similar capabilities to Dameware Remote Everywhere. DRS incorporates Dameware Mini Remote Control, allowing for multi-platform remote access to Windows, Mac, and Linux devices.
DRS offers unlimited endpoint agents per license, and it allows for mass deployment of agents to devices and integration with help desk software. The tool includes around-the-clock remote assistance and the ability to manage Active Directory environments and deliver support from iOS and Android devices.
If you’re wondering which SolarWinds product is right for your business, the company provides a comprehensive comparison of DRE and DRS. Both solutions offer free trials to help you decide.
RemotePC
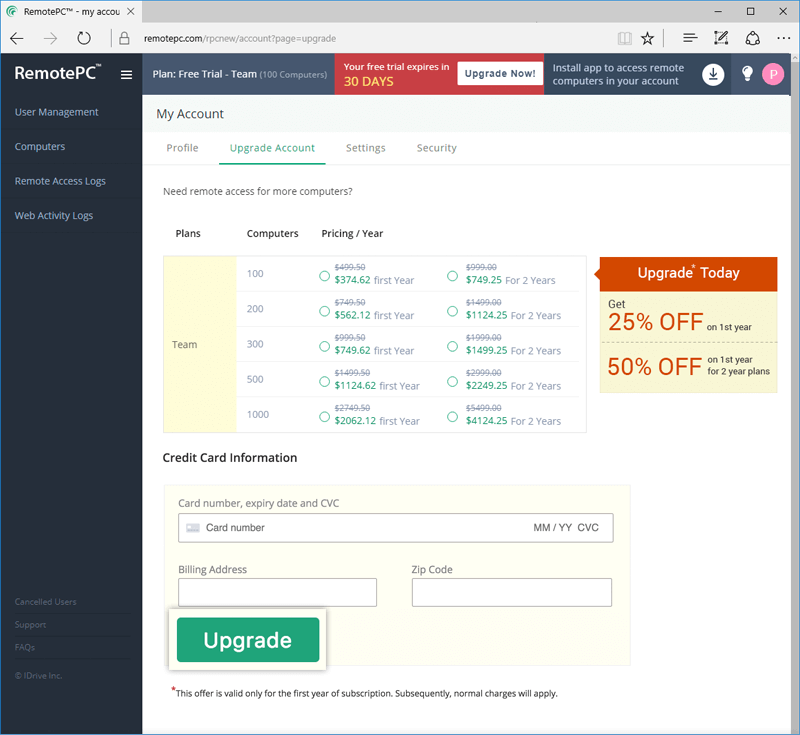
I like RemotePC from IDrive because of how easy it is to use. It has a shallow learning curve, so even new technicians can hit the ground running with this remote support tool. Installation is simple and straightforward, and remote devices are typically verified in seconds. Once the program is up and running, IT technicians can use it to transfer files, chat with end users, print remotely, etc.
The capabilities in RemotePC are extensive, but they aren’t nearly as exhaustive as those in DRE. RemotePC is a great choice for companies looking for an uncomplicated program designed to get the job done well without a bunch of bells and whistles. If you’re looking for something more sophisticated and capable of running local batch scripts or performing reboots and reconnects, I suggest going with SolarWinds DRE.
TeamViewer
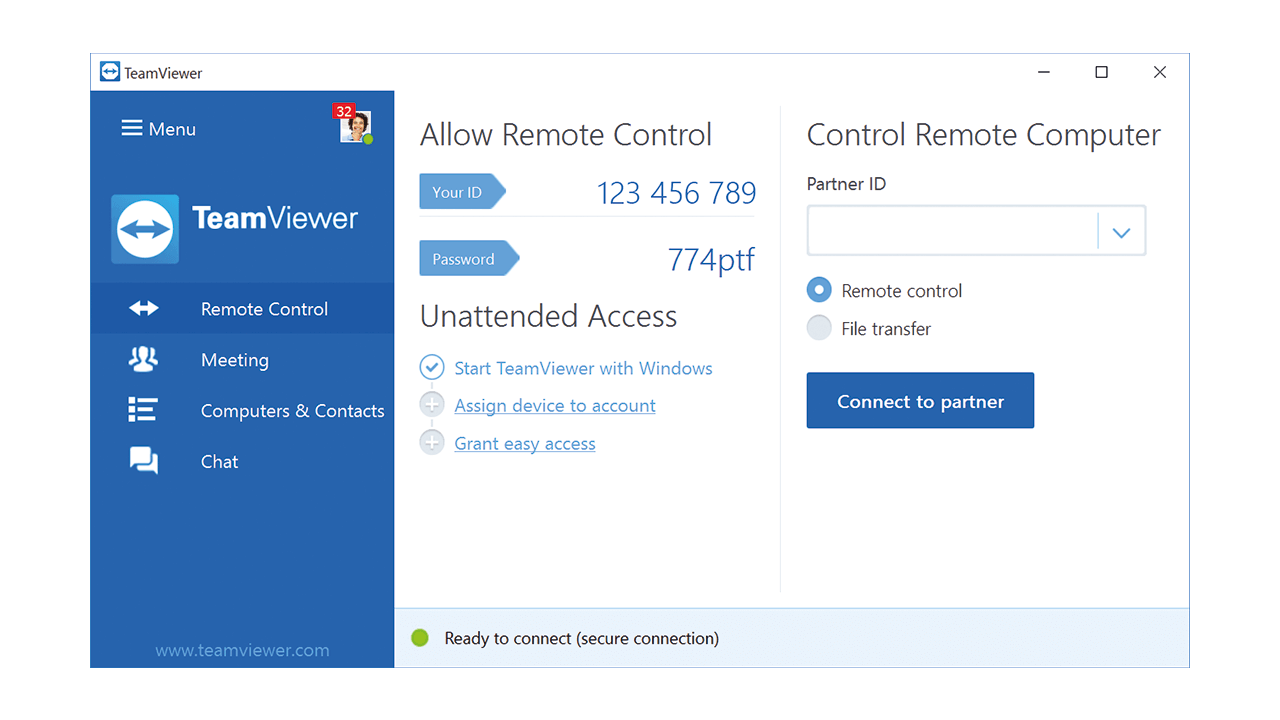
TeamViewer was designed with large enterprises in mind. Shared meeting tools and remote support unite in this tool, helping employees in offices across the globe increase their productivity and remain connected. Versatility is the name of the game with TeamViewer: it’s available on Windows, OS X, Linux, Android, and iOS; it can connect to out-of-band computers; and it facilitates file transfers, iOS screen sharing, and much, much more.
Due to its extensive capabilities and reach, TeamViewer comes with a hefty price tag. The cost is worth it for major corporations, but smaller organizations will likely find it prohibitive.
Zoho Assist
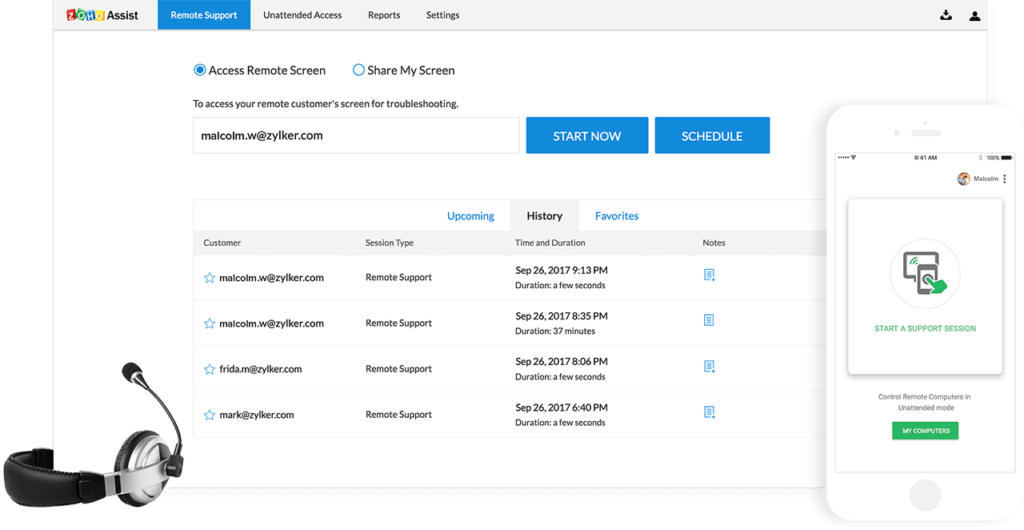
At the other end of the spectrum is Zoho Assist. This tool was built with small businesses in mind—especially those without a sophisticated help desk system. But while Zoho Assist is not as robust as other remote access software, it’s still incredibly powerful. Users of the platform are equipped to set up unattended remote access and manage remote PCs, laptops, mobile devices, and servers with unparalleled ease. It only takes a few seconds to provide customers with the support they need to get up and running again.
In addition, Zoho Assist offers file transfer, instant chat, and remote print, just like the other big dogs. If you’re charged with managing the IT of a small business, this cost-effective tool may be exactly what you’re looking for.
Splashtop

I love Splashtop because it provides two unique services: remote desktop for individuals and teams and remote control for IT and support teams. Each service is unique, and both are highly effective. With Splashtop remote desktop, employees can access their Windows PCs and Macs from their smartphones, tablets, or any other computer. This makes it easy to transfer files, remote print, and more while on the go or working from home.
For IT technicians, Splashtop remote support enables unattended remote access to quickly resolve end-user issues. Its features include remote wake and reboot, session recording, in-session chat, and more. But even though an unlimited number of technicians can use the platform, you’ll be charged per unattended endpoint.
Take Control
Last but not least, let’s look at Take Control. This is a specialized tool for Managed Service Providers (MSPs), designed to help you provide IT support at scale without overcomplicating or slowing down the process.
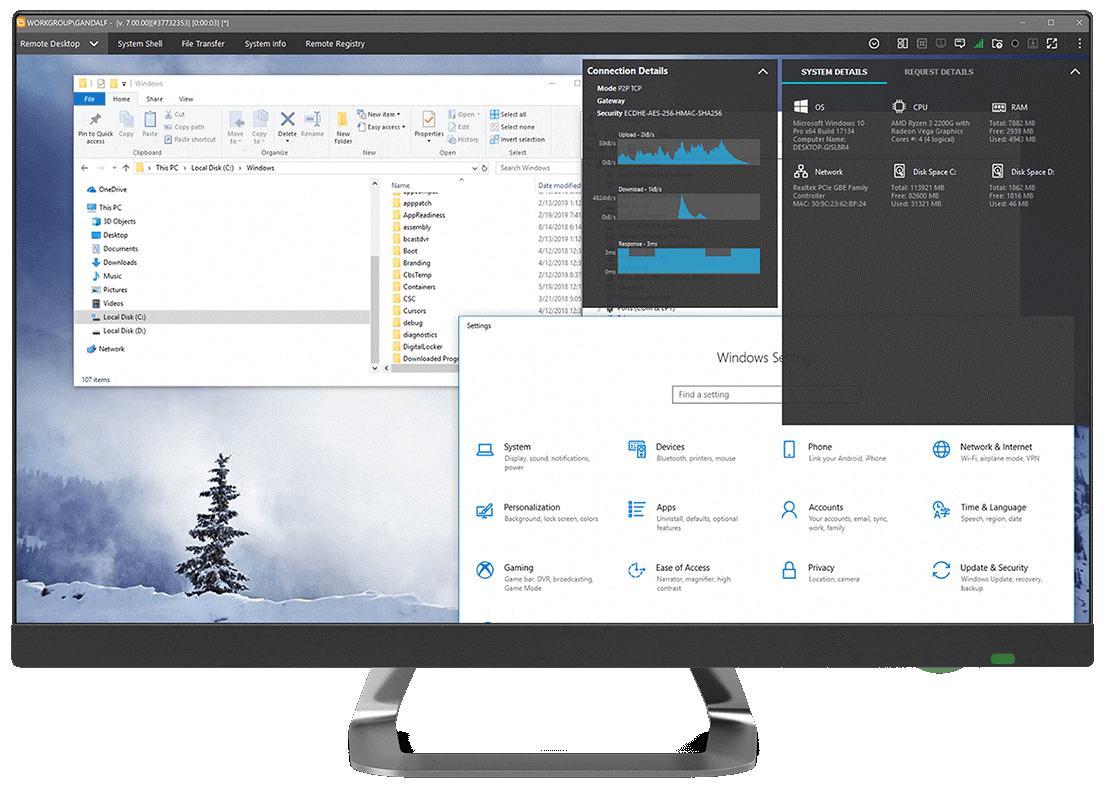
Take Control is remote support software that provides a handy centralized dashboard. From there, you can view in-depth diagnostics for your clients’ devices and networks. It can connect to remote devices in just seconds, making it easy to provide top-notch customer service.
Another great thing about Take Control is that it provides a full suite of customization options. This enables you to configure the software to meet your specific needs, and even add in your own custom branding.
Best Free Remote Desktop Software
While my picks for the best paid remote desktop software are listed above, there are also many free versions if budgets are tight. These platforms aren’t as complex as their paid counterparts, but they can still help you remotely manage the workstations, storage, and network resources scattered across your company’s offices. Here are a few of my favorites:
Chrome Remote Desktop
Chrome Remote Desktop is a basic tool for free remote desktop connections, but don’t be fooled by its simplicity. Users can leverage the platform to connect to their desktops while traveling or working from home as long as the client and host computer have Chrome installed. This means files, folders, and must-have documents are right at their fingertips, keeping productivity high.
Chrome Remote Desktop is great for remote connections, but its overall service offerings are limited in scope. This is the perfect introductory tool for any young company looking to dip its toes into the world of remote access.
Microsoft Remote Desktop

Like Chrome Remote Desktop, Microsoft Remote Desktop is a simple and effective tool for achieving remote connections. This platform can help users remotely access Windows PCs from other Windows computers, mobile devices, and Macs. Though you can use a MAC to access a Windows PC, the opposite (using a Windows PC to access a MAC) won’t work.
Windows Remote Desktop is compatible with devices with Windows 7 or higher.
Remote Utilities
Remote Utilities offers an impressive array of features for a US$0 price tag. To get the program up and running, simply pair two computers via an internet ID and you’re good to go. Once the connection has been made, a viewer appears to help facilitate control from whatever device you’re using as the controller. A host can be installed on a remote computer for unattended access, and spontaneous access is secured through a run-only agent. Remote Utilities is perfect for those looking for a more advanced—but still free—remote access option.
Remote Access Simplified
Remote work is rapidly becoming the norm in a vast array of industries. Employees are now opting to work from home, take their roles on the road, or relocate to satellite offices more suited to their lifestyle. Companies are seeing higher employee engagement and greater results because of this flexibility.
But even though the perks of remote, dispersed teams are many, there are also significant challenges—most notably, the ability to provide crucial IT support. Fortunately, technology has evolved with the times. IT administrators and their support technicians can leverage remote access software to accomplish everything from password resets to application troubleshooting while thousands of miles away. Remote employees are no longer left stranded when faced with a challenging tech issue.
Of all the available remote access tools, my favorite is Dameware Remote Everywhere from SolarWinds. I have yet to find a tool capable of beating its price while maintaining a high level of security and competitive service offerings. But don’t take my word for it—register for a 14-day free trial and see for yourself.
Source:https://www.dnsstuff.com/what-is-remote-access-definition#what-is-remote-desktop-access Date: 08.12.2020г.